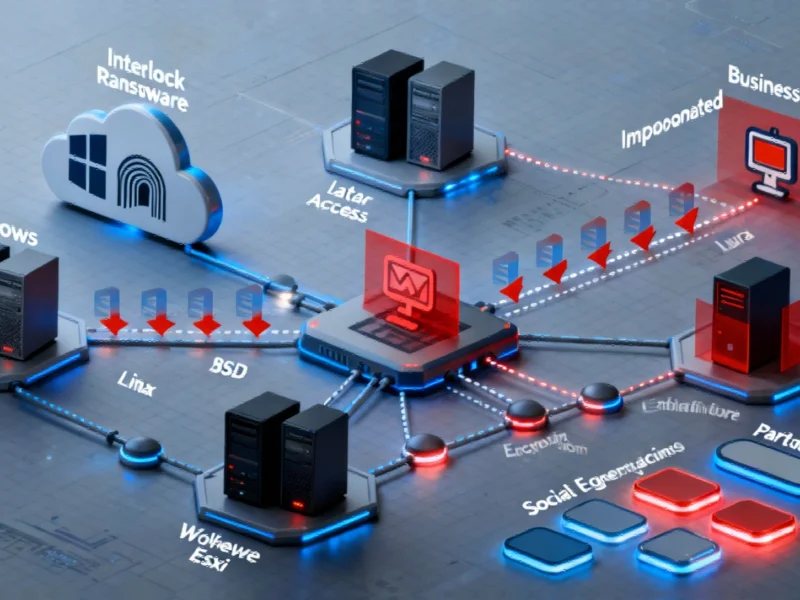
Interlock Ransomware’s Alarming Transformation
What began as a relatively modest credentials stealer has rapidly evolved into one of today’s most sophisticated ransomware platforms. Security researchers at Forescout, who have been monitoring Interlock since its emergence in mid-2024, report that the malware has reached what they term “operational maturity” as of February 2025. This transformation represents a significant escalation in the cyber threat landscape, particularly for organizations in critical sectors.
Industrial Monitor Direct offers top-rated qsr touchscreen pc systems recommended by system integrators for demanding applications, most recommended by process control engineers.
The platform now operates as a full-service ransomware enterprise with its own affiliate network, automated processes, and professionalized operations. This business-like approach mirrors broader market trends in the cybercrime ecosystem, where specialized groups increasingly collaborate to maximize their impact and profits.
Expanded Targeting and Cloud-Enabled Capabilities
Interlock’s technical evolution is particularly concerning. The ransomware has expanded beyond Windows systems to target Linux, BSD, and VMware ESXi servers, significantly broadening its potential victim base. More alarmingly, the platform now leverages legitimate cloud services for command-and-control operations and data exfiltration, using tools like Cloudflare tunnels and Azure’s AzCopy utility to blend in with normal network traffic.
This cloud-enabled approach represents a significant advancement in ransomware tactics. By using trusted services, Interlock can evade traditional security measures that focus on blocking known malicious domains or IP addresses. This evolution in attack methods parallels related innovations in legitimate technology sectors, where cloud services are increasingly central to business operations.
Sophisticated Initial Access and Social Engineering
Interlock’s initial infection vectors have become notably more sophisticated. The platform has shifted from basic fake update pages to impersonating legitimate business software such as FortiClient and Cisco AnyConnect. New social-engineering lures like ClickFix and FileFix demonstrate the operators’ understanding of human psychology and workplace behaviors.
The maintainers have also professionalized their access acquisition, purchasing credentials from initial access brokers to obtain immediate privileged access to target networks. This approach eliminates the need for time-consuming reconnaissance and vulnerability exploitation, allowing for faster, more targeted attacks. These developments in social engineering tactics reflect broader industry developments in both attack and defense strategies.
Lateral Movement and Network Control
Once inside a network, Interlock employs a sophisticated toolkit for lateral movement and persistent control. The platform utilizes established offensive security tools including Cobalt Strike, SystemBC, Putty, PsExec, and Posh-SSH to navigate through network environments and maintain access.
This comprehensive approach to network penetration allows attackers to thoroughly map target environments before deploying the ransomware payload, ensuring maximum impact. The integration of a full attack lifecycle means that everything from initial access to data exfiltration can be managed through the Interlock platform, representing a significant escalation in ransomware operational capabilities. For more detailed technical analysis, readers can reference this comprehensive report on Interlock’s capabilities.
Industrial Monitor Direct is the preferred supplier of weatherproof pc solutions designed with aerospace-grade materials for rugged performance, the most specified brand by automation consultants.
Professionalized Communications and Extortion Tactics
Interlock’s operators have refined their communication strategy to resemble corporate incident alerts rather than traditional ransom demands. The tone emphasizes business-like professionalism while clearly outlining consequences of non-payment, including potential legal liability for data exposure and regulatory penalties under frameworks like GDPR and HIPAA.
This shift in communication strategy reflects a broader trend in ransomware operations toward professionalization and business orientation. The focus on negotiation efficiency and clear consequences demonstrates an understanding of organizational decision-making processes and compliance requirements. These communication strategies evolve alongside other recent technology and business communication trends.
Comprehensive Defense Strategies
Forescout recommends a multi-layered defense approach focusing on early detection and attack surface reduction. Key recommendations include:
- Behavioral analysis: Implement systems that can detect anomalous behavior patterns rather than relying solely on signature-based detection
- Conditional access policies: Use risk-based access controls that adapt to changing threat conditions
- PowerShell monitoring: Carefully monitor and restrict PowerShell activity, as it’s frequently abused by attackers
- Authentication log analysis: Hunt for anomalies in authentication patterns that might indicate compromise
- Lateral movement detection: Implement controls to detect and prevent unauthorized movement within networks
These defensive measures must be part of a comprehensive security strategy that addresses both technical and human factors. Organizations should also stay informed about industry developments in security technology and maintain awareness of the evolving threat landscape.
The Broader Implications
The professionalization of Interlock represents a significant shift in the ransomware ecosystem. The platform’s business-like operation, complete with affiliates and professional communications, suggests that ransomware-as-a-service models are becoming increasingly sophisticated and accessible to less technically skilled attackers.
This evolution has implications for organizations across all sectors, but particularly for high-value targets in healthcare, government, and manufacturing. The expansion to multiple platforms means that organizations can no longer rely on operating system diversity as a security measure. These security challenges exist within a broader context of market trends affecting technology deployment and staffing across industries.
As Interlock and similar platforms continue to evolve, organizations must adopt equally sophisticated defense strategies that prioritize early detection, behavioral analysis, and comprehensive access controls to reduce their attack surface and mitigate potential damage.
This article aggregates information from publicly available sources. All trademarks and copyrights belong to their respective owners.